CYBER SECURITY
-

Positiv denken für Sicherheitsentscheider: 6 Mindsets, die Sie sofort ablegen sollten
Security wiederum ist wie Qualität kein fertiges Produkt, sondern (wie bereits angemerkt) eine fortlaufende Disziplin. Sicherheit als eine Praxis zu…
Read More » -
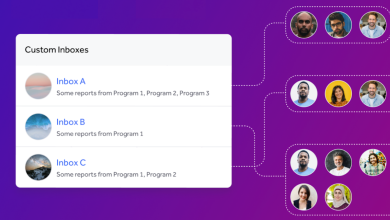
Streamline Report Management with Custom Inboxes: Reducing Delays and Security Risks
Introducing Custom Inboxes Custom Inboxes provide our enterprise customers with unparalleled flexibility in report management. Now, organizational administrators can create,…
Read More » -

Irish Watchdog Imposes Record €310 Million Fine on LinkedIn for GDPR Violations
Oct 25, 2024Ravie LakshmananDigital Advertising / Privacy The Irish data protection watchdog on Thursday fined LinkedIn €310 million ($335 million)…
Read More » -

SEC Charges 4 Companies Over Misleading SolarWinds Cyber Attack Disclosures
Oct 25, 2024Ravie LakshmananRegulatory Compliance / Data Breach The U.S. Securities and Exchange Commission (SEC) has charged four current and…
Read More » -

Change Healthcare data breach exposed ‘only’ 100 million US health records
Payments to healthcare providers, which are typically processed by Change Healthcare, were abruptly halted as the company took systems offline…
Read More » -

Black Hat USA 2024 recap – Week in security with Tony Anscombe
Video Unsurprisingly, many discussions revolved around the implications of the CrowdStrike outage, including the lessons it may have offered for…
Read More » -
Is Your Identity Security AI-Proof?
Oct 25, 2024The Hacker NewsArtificial Intelligence / Identity Security Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to…
Read More » -

Vulnerability Deep Dive: Gaining RCE Through ImageMagick With Frans Rosen
The file upload vulnerability type is as broad in scope as the number of different file types. These vulnerabilities are…
Read More » -

Predictable AWS cloud deployment resources allow full account takeover
S3 bucket name-squatting CDK is AWS’ open-source framework organizations use to define their infrastructure as code (IaC), the process of…
Read More » -

Four REvil Ransomware Members Sentenced in Rare Russian Cybercrime Convictions
Oct 26, 2024Ravie LakshmananCybercrime / Malware Four members of the now-defunct REvil ransomware operation have been sentenced to several years…
Read More »
