Hacking
-

Introducing HackerOne’s Hai API: Revolutionize Your Workflow Automation with AI
Unlocking the Power of the Hai API At HackerOne, we believe in practicing what we preach. To help get an…
Read More » -
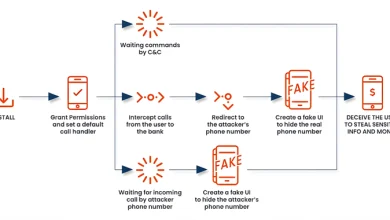
New FakeCall Malware Variant Hijacks Android Devices for Fraudulent Banking Calls
Nov 04, 2024Ravie LakshmananMobile Security / Financial Fraud Cybersecurity researchers have discovered a new version of a well-known Android malware…
Read More » -

The cyberthreat that drives businesses towards cyber risk insurance
Business Security Many smaller organizations are turning to cyber risk insurance, both to protect against the cost of a cyber…
Read More » -
What HackerOne Customers Say About Remediating Vulnerabilities and Getting the Best Results From Hackers
Remediating Vulnerabilities Streamlining communication between hackers and security teams, HackerOne customers are able to quickly and thoroughly remediate vulnerabilities before…
Read More » -
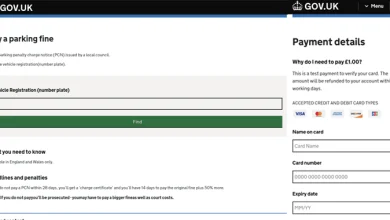
New Phishing Kit Xiū gǒu Targets Users Across Five Countries With 2,000 Fake Sites
Cybersecurity researchers have disclosed a new phishing kit that has been put to use in campaigns targeting Australia, Japan, Spain,…
Read More » -

AI and automation reduce breach costs – Week in security with Tony Anscombe
Video Organizations that leveraged AI and automation in security prevention cut the cost of a data breach by $2.22 million…
Read More » -
What Is the Digital Operational Resilience Act (DORA)?
DORA focuses on Information and Communications Technology (ICT) systems and applies to all financial institutions in the EU. This includes…
Read More » -

5 SaaS Misconfigurations Leading to Major Fu*%@ Ups
Nov 01, 2024The Hacker NewsSaaS Security / Insider Threat With so many SaaS applications, a range of configuration options, API…
Read More » -

Why tech-savvy leadership is key to cyber insurance readiness
Business Security Having knowledgeable leaders at the helm is crucial for protecting the organization and securing the best possible cyber…
Read More » -
Pentesting for Web Applications: Methodologies & Best Practices
Pentest reports are a requirement for many security compliance certifications (such as ISO 27001 and SOC 2), and having regular pentest reports…
Read More »
