Hacking
-

U.S. Charges Three Iranian Nationals for Election Interference and Cybercrimes
U.S. federal prosecutors on Friday unsealed criminal charges against three Iranian nationals who are allegedly employed with the Islamic Revolutionary…
Read More » -

Analysis of toolset used to spy on Ukraine in 2022 and 2023
ESET Research ESET Research has conducted a comprehensive technical analysis of Gamaredon’s toolset used to conduct its cyberespionage activities focused…
Read More » -

A Guide to Subdomain Takeovers
1. Understanding subdomain takeovers 2. Identifying vulnerable services 3. Examples of vulnerable and secure services 4. Enumerating subdomains 5. Automating…
Read More » -
DockerSpy Searches For Images On Docker Hub And Extracts Sensitive Information Such As Authentication Secrets, Private Keys, And More
DockerSpy searches for images on Docker Hub and extracts sensitive information such as authentication secrets, private keys, and more. What…
Read More » -

How to Evaluate and Choose the Best Web Hosting Service – Latest Hacking News
40 Understanding Your Hosting Needs What kind of website are you going to host? It may be a blog, an…
Read More » -
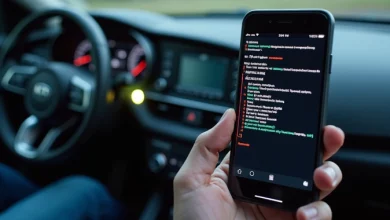
Hackers Could Have Remotely Controlled Kia Cars Using Only License Plates
Sep 26, 2024Ravie LakshmananAutomotive Industry / Technology Cybersecurity researchers have disclosed a set of now patched vulnerabilities in Kia vehicles…
Read More » -

Don’t panic and other tips for staying safe from scareware
Digital Security Keep your cool, arm yourself with the right knowledge, and other tips for staying unshaken by fraudsters’ scare…
Read More » -

HackerOne’s Commitment to Learning and Development
HackerOne is committed to providing comprehensive learning and development opportunities to fuel our competitive edge and cultivate a highly skilled…
Read More » -

Vulnerable-Drone – An Intentionally Vulnerable Drone Hacking Simulator Based On The Popular ArduPilot/MAVLink Architecture, Providing A Realistic Environment For Hands-On Drone Hacking
The Damn Vulnerable Drone is an intentionally vulnerable drone hacking simulator based on the popular ArduPilot/MAVLink architecture, providing a realistic…
Read More » -

How to check suspicious links fast? – Latest Hacking News
68 Nowadays, the most popular security measures against phishing links include automated checks and blocking suspicious links before they reach…
Read More »
