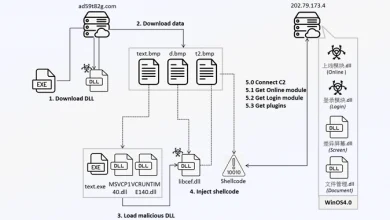
VMware patches security vulnerability twice

The vulnerability is a heap overflow in the implementation of the DCERPC (distributed computing environment / remote procedure call) protocol in vCenter Server. An attacker with network access to vCenter server can trigger them by sending a specially crafted network packet, which can then lead to a remote code execution. That’s why the vulnerability is so dangerous and is rated with a CVSS severity rating of 9.8/10.
Hackers from China found the vulnerability
When the first patch was released in September 2024, VMware attributed the discovery of the issues to research teams participating in the 2024 Matrix Cup, a hacking competition in China that uncovers zero-days in major operating system platforms, smartphones, enterprise software, browsers and security products.
The Matrix Cup competition took place in June 2024 and is sponsored by Chinese cybersecurity firm Qihoo 360 and Beijing Huayun’an Information Technology.